 Technicians at computer security firm Kapersky Labs have linked a software code in the Flame virus to the Stuxnet cyber weapon, proving the teams responsible for the malware collaborated in the early stages of the development.
Technicians at computer security firm Kapersky Labs have linked a software code in the Flame virus to the Stuxnet cyber weapon, proving the teams responsible for the malware collaborated in the early stages of the development.
Kapersky Labs chief security expert Alexander Gostev said: "The new findings that reveal how the teams shared source code of at least one module in the early stages of development prove that the groups co-operated at least once.
"What we have found is very strong evidence that Stuxnet/Duqu and Flame cyber-weapons are connected," a company statement confirmed.
Symantec Corp, the world’s largest security firm, later echoed Kapersky’s sentiments, stating that some source code had been shared.
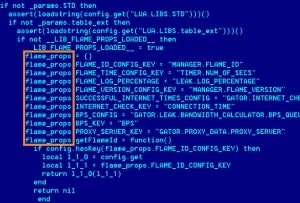
The link is related to a module found in early versions of the Stuxnet malware named ‘Resource 207’, with the module bearing a strong resemblance to code used in Flame.
"The list includes the names of mutually exclusive objects, the algorithm used to decrypt strings, and the similar approaches to file naming," Gostev added.
How well do you really know your competitors?
Access the most comprehensive Company Profiles on the market, powered by GlobalData. Save hours of research. Gain competitive edge.

Thank you!
Your download email will arrive shortly
Not ready to buy yet? Download a free sample
We are confident about the unique quality of our Company Profiles. However, we want you to make the most beneficial decision for your business, so we offer a free sample that you can download by submitting the below form
By GlobalDataThe uncovered link is now highly likely to fuel increasing speculation that both Stuxnet and Flame are part of a US-led cyber campaign, forged with Israeli cooperation and designed to target Iran’s nuclear programme. Despite the target appearing to be Iranian nuclear facilities, computers across the globe have been infected, prompting cyber security reviews.
A recent New York Times investigation alleged that the US was responsible for Stuxnet, created under orders from US President Barack Obama. Discovered in 2010, Stuxnet caused damage to centrifuges at a uranium enrichment facility in Natanz, Iran by causing them to accelerate.
Flame, however, is a vastly more complex programme, with many labelling it as the most complex malware ever discovered. Containing 20 times as much code as Stuxnet, it targeted government and energy-industry offices in several Middle Eastern countries before its creators sent a ‘suicide’ command, instructing the virus to remove itself from computers and replace itself with nonsensical code, designed to prevent technicians from deciphering it.
When accused of instigating the development of Stuxnet, US authorities refused to make denials and instead launched investigations into leaks surrounding the classified project. The White House has since refused to comment.
With speculation continuing to mount and investigations into the Flame virus ongoing, the US will face growing questions about the intention of any potential cyber warfare programme.
The United Nations has asked security experts to follow up Iranian requests to assess the damage caused to computers, and any further evidence linking the US or Israel to such an attack is highly likely to trigger an international incident with the covert operations brought into the open.
Image: A screenshot by Kaspersky Lab of source code of the Flame computer worm.







