
According to documents leaked to the press by former National Security Agency (NSA) and Central Intelligence Agency (CIA) analyst Edward Snowden, US security agencies have gathered millions of phone records and monitored internet data in what could represent a worldwide invasion of privacy in the name of counter-terrorist operations.
Labelled as an "existential threat to democracy" by Snowden, the documents detail how the US ordered mobile telecommunications provider Verizon to hand over metadata relating to millions of phone calls, including phone numbers, duration, time and the approximate location.
Also detailed is the existence of a programme entitled Prism, tasked with tapping into online companies including Facebook, Google, Microsoft and Yahoo, in order to track online communications through e-mails and web chats. Each company has refused to grant the US Government with direct access to such material, with analysts suggesting that a specific target may have to be named first before information can be requested.
The Washington Post has expanded to allege that the NSA even possesses the ability to conduct live surveillance of someone doing a Google search."We can plant bugs in machines. Once you go on the network, I can identify your machine. You will never be safe whatever protections you put in place," Snowden explained to the Guardian.
See Also:
What this has come to illustrate is the mountains of data collated by intelligence agencies, and the technology designed to decipher such a mammoth task.
How well do you really know your competitors?
Access the most comprehensive Company Profiles on the market, powered by GlobalData. Save hours of research. Gain competitive edge.

Thank you!
Your download email will arrive shortly
Not ready to buy yet? Download a free sample
We are confident about the unique quality of our Company Profiles. However, we want you to make the most beneficial decision for your business, so we offer a free sample that you can download by submitting the below form
By GlobalDataMonitoring the intel flow
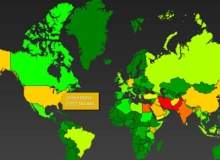
In order to monitor and collate such data, documents leaked by Snowden reveal that the NSA developed a tool with which to record and analyse the origins of intelligence. Dubbed ‘Boundless Informant’, the system maps where intelligence originates from by country and displays this information on a map, with countries colour-coded to indicate the concentration of data from one country compared to another.
Leaked documents state the tool "allows users to select a country… and view metadata volume and select details about the collections against that country."
During a 30-day period ending in March 2013, the tool shows that the NSA collected some 14bn pieces of intelligence from Iran, 13.5bn from Pakistan and three billion pieces from the US.
The aim of Boundless Informant would appear to be to identify pattern recognition rather than outright spying, with documents claiming the tool to answer questions "like ‘What type of coverage do we have on country X’ in near real-time by asking the SIGINT infrastructure."
Existence of Boundless Informant seemingly defies statements made by NSA spokeswoman Judith Emmel, claiming that the NSA lacks the ability to reliably track the origin of intelligence and, in turn, cannot determine which intelligence comes from a US-based source. Furthermore, US President Barack Obama moved to appease the US public by categorically stating "nobody is listening to your telephone calls."
Obama’s statement is strictly true – the content of such intercepts is explicitly protected by the Fourth Amendment of the US Constitution – but the obvious desire of the US to not just collect, but filter, metadata using Boundless Informant must pour scorn on the NSA’s repeated claims that the agency lacks the technological capability for targeted communications surveillance. The existence of Boundless Informant shifts this question from who, to what, might be listening.
An ethical dilemma
Despite the NSA assuring Congress that it cannot keep track of the surveillance it performs on communications emanating from the US, these documents would infer that the NSA does maintain the ability to break down surveillance intercepts. Given the collation of metadata taking place, it is entirely plausible that the agency could, in fact, determine how many intercepts originate from the US given how the tool includes detail down to individual IP addresses.
While the NSA insists they only monitor metadata, it is this level of detail present in the metadata that allows intelligence agencies to compile more complex profiles of potential terrorists. In a previous interview with Army Technology, i2 CEO Bob Griffin said: "Analysis tools help identify rising stars in any community as they have the most links to anyone else and may be a communications facilitator, because people in the network only communicate with specific trusted individuals."
Griffin further elaborates on a social network analysis of the al-Qaeda network conducted around the time of Osama Bin Laden’s capture that despite Al Zahawiri being al-Qaeda’s heir apparent, he was not even in the top three of members with the most connections.
Therefore, the debate over what constitutes an invasion of privacy and what must be regarded as a necessary evil remains. Boundless Informant will undoubtedly divide opinion, with many considering such snooping unconstitutional. However, the use of metadata in such a way that forming patterns can indicate towards potential terrorist suspects, both domestic and overseas, is perhaps a weapon too strong to be ignored and restricted by red tape.
An opportunistic back-door entrance?
Evidently, Boundless Informant is a highly advanced tool capable of collecting and processing enormous levels of data into accessible and manageable amounts, in order to assist counter-terror operations.
If Snowden and leaked documents are to be believed, the tool is only due to get more advanced and more powerful as upgrades roll out in the coming months.
Perhaps more pertinent, however, is the growing opinion that operations like this, and Prism in particular, have been seen as opportunistic windows of installing back door entrances into the world’s communications providers prior to the emergence of a level of data encryption that would all but render such surveillance impossible.
The existence and sophistication of Boundless Informant implies the level of thought that has gone into communication surveillance on a global scale, while also bringing doubt over the US Government’s continuous assertions that it lacks the wherewithal to differentiate between domestic and overseas chatter.
Related content
Video feature: changing LAWS of warfare – US laser weapon downs drones
Having been the subject of interest of military commanders and science-fiction fans alike for decades, the US Department of Defense believes it is finally making ground in the pursuit of laser weaponry following a successful test of its LAWS system.
The hole in the fence – Israel’s Waterfall Security talks cyber security
With digital systems increasingly controlling real-world assets, protecting critical infrastructure is no longer simply about denying physical access.


.gif)





